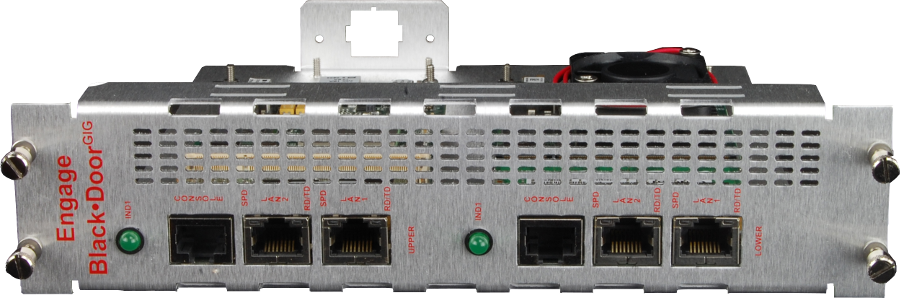
BlackDoor GIG
Packet Encryptor
BlackDoor GIG
Packet Encryptor

SIZE
9" (L) x 7.3” (W) x 1.50” (H)
Overview
Gigabit Ethernet - Layer 2/3/VLAN/MPLS Encryption
The Engage Black•Door GIG Encryptor offers customers a new level of Gigabit speeds for securing existing packet based networks. The AES based encryption algorithms offer industry standard security levels at multiple layers of the network OSI while supporting up to Gigabit Ethernet transmission speeds. The Black•Door GIG Encryptor is installed at the edge of the existing network interfaces and means instant security upgrades for customer satisfaction and network invisibility.
The Black•Door GIG is used by customers around the world for enterprise network security; it has always offered a reliable, efficient, cost-effective solution for adding encryption to non-secure network interfaces. It provides this level of security without requiring new system software or having to upgrade existing network edge devices. The Black•Door GIG Encryptor gives customers wanting a higher level of network protection a faster network alternative, a Gigabit interface encryption machine.
The Black•Door GIG Encryptor enables enterprises to add AES security to Ethernet packet interfaces without having to disrupt their network edge hardware with upgrades, reconfiguration and add-on encryption accelerators. The Black-Door is deployable with basic Internet Protocol knowledge.
Independently configurable MTUs with 9000 byte JUMBO Ethernet Support
The Engage Black•Door GIG Encryptor offers customers a new level of Gigabit speeds for securing point to point or multi-point Ethernet networks. The Black•Door GIG Encryptor’s Ethernet interfaces have independently configurable MTUs that are able to handle up to 9000 byte JUMBO Ethernet frames in real-time. The AES based encryption algorithm offer industry standard security levels at Layers: 2/VLAN/MPLS/3.
Point to Point “Plug-and-Encrypt” Installation
The Change to Connectionless Networks
Ethernet networks are being used for larger scale networks and as a replacement for traditional telco data services. Both private enterprises as well as service providers see the proliferation of Ethernet as a backhaul medium as an advantage for their network expansion. However, Ethernet at this scale can also lead to potential issues as the network is no longer as secure as a connection-oriented infrastructure. Security interfaces are required at all network access points to assure data packets as well as address information is encrypted and protected. These interfaces might be less robust software solutions or for a higher level of network security, plug-and-play encryption appliances.
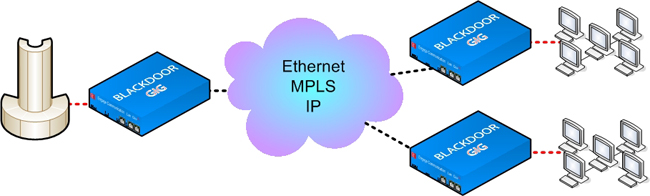
These interfaces might be less robust software solutions or for a higher level of network security, plug-and-play encryption appliances. The Engage Black•Door GIG Encryptor offers an effective, easy-to-install solution to solve this problem. The Black•Door GIG Encryptor can be added to existing equipment sites for upgrade of security or it can be installed with new systems to add AES encryption to non-secure equipment. It works in both point-to-point as well as point-to-multi-point configurations at Gigabit access speeds.
OSI Layer Encryption
Layer 2 - Bridge
Interfaces at Layer 2, non-local packets are encrypted above the MAC layer and then directed to the appropriate destination address by the internal bridge.
Layer 3 - Router
Interfaces at Layer 3, packets are encrypted above the Network Layer and then can be dynamically or statically routed to the destination network by the internal router.
Tunnel - Equipment Interface
Many times network to network security requires an encrypted ‘tunnel’ carrying Ethernet packets over a pre-defined network path. The Black•Door GIG Encryptor permits user creation of a destination table, encrypts the entire incoming packet, and adds the appropriate destination address for correct network transport.
MPLS
Multi-Protocol Label Switching offers a path oriented address which can direct packets to a specific end address over a ‘virtual’ private path to a destination network. A virtual private path does not, however, guarantee data packet security. The Black•Door GIG Encryptor can provide ‘payload only’ encryption for MPLS data packets, maintaining the MPLS labels while encrypting the MPLS payload. It is flexible enough to provide an encrypted ‘tunnel’ for point-to-point MPLS connections or can encrypt at Layer 2 or Layer 3 or both, easy to configure without any down time for network access equipment.
Point-to-Point or Point-to-Multi-point Network Configurations
The Black•Door GIG Encryptor transparently AES encrypts Ethernet networks at Gigabit speeds. Ethernet Voice, Video or Data packets, that are destined for a device located on a remote network or a different local network segment, are AES encrypted at the Link, Network or Transport Layer and then tunneled, bridged or routed to the destination network. At the destination network the packets are decrypted and the original Ethernet packets are securely delivered to the destination Ethernet device.
Applications
- AES Encryption for Layer 2/3 Payloads
- Point-to-Multi-Point with Multiple Key Support
- Gigabit Ethernet Payload - Supports JUMBO Ethernet Frames
- MPLS Data Payload Encryption
- Plug-and-Play Functionality
- 256 Bit AES Keys
The BlackDoor GIG Ethernet Encryptor meets the new security requirements and reduces overall network complexity for:
- Department of Defense - Air Force, Army, Navy, Marines
- National, State and Local Governments
- Public Safety Networks
- Homeland Security
- Multi-Site Commercial Enterprises
- Banking and Financial Institutions
- Health Care Industries
- Natural Gas & Electric Power Utility Companies
- Transportation Agencies
- Closed Circuit TV
BlackDoor GIG enables Enterprises to achieve the stringent information security standards that are mandated by a variety of legislative actions, including the Health Insurance Portability and Accountability Act, Sarbanes-Oxley, California Database Security Breach Act, the Gramm-Leach-Bliley Act, EU Data Protection Directive and the Federal Information Security Management Act.
BlackDoor GIG enables Enterprises to prevent network attacks that seek to obtain or manipulate their most vital or profitable sources of information including:
- Customer Records
- Intellectual Property
- Marketing Plans
- Employee Files
- Accounting Forecasts
- Sales Strategies
- Source Code
- Formulae
- Financial Spreadsheets
Network to Multiple Network Access Points - Encryption with BLACKDOOR GIG Encryptor
Broadband Interoffice Ethernet
Demand for interoffice bandwidth to support applications such as: VOIP, IPTV and Video on Demand, and the aggressive pricing from Ethernet Service providers are pushing Interoffice Ethernet into Multisite Enterprises. Encryption is required at all network access points to assure sensitive payload and address information is encrypted and protected when it traverses service provider networks
Wireless Gigabit Ethernet Encryption
One of the most economical means to establish Gigabit Ethernet connectivity between line-of-site locations is Wireless Ethernet with Gigabit interfaces. The BlackDoor GIG facilitates encryption of the Egress Ethernet to externally located Wireless Gigabit and offloads encryption from the Radio and supports multi point installations.
Connectionless Network Protocol Security
Ethernet networks are being used for larger scale networks and as a replacement for traditional telco data services. Both private enterprises as well as service providers see the proliferation of Ethernet as a backhaul medium as an advantage for their network expansion. However, Ethernet at this scale can also lead to potential issues as the network is no longer as secure as a connection-oriented infrastructure.
Security interfaces are required at all network access points to assure data packets as well as address information is encrypted and protected. These interfaces might be less robust software solutions or for a higher level of network security, plug-and-play encryption appliances. The Engage BlackDoor GIG offers an effective, easy-to-install solution to solve this problem. The BlackDoor GIG can be added to existing equipment sites for upgrade of security or it can be installed with new systems to add AES encryption to non-secure equipment. It works in both point-to-point as well as point-to-multi-point configurations at Gigabit access speeds.

Note: the BlackDoor GIG has interoperability with the BlackDoor 10/100 that supports 10 and 100 BaseT Ethernet.
OSI Layer Encryption - BLACKDOOR GIG Encryptor Benefits
OSI Layer
Solution/Benefit
Layer 2 - Bridge
Interfaces at Layer 2, non-local packets are encrypted above the MAC layer and then directed to the appropriate destination address by the internal bridge.
Layer 3 - Router
Interfaces at Layer 3, packets are encrypted above the Network Layer and then can be dynamically or statically routed to the destination network by the internal router.
Layer 2.5 - MPLS
The BlackDoor GIG can provide ‘payload only’ encryption for MPLS data packets, maintaining the MPLS labels while encrypting the MPLS payload. It is flexible enough to provide an encrypted ‘tunnel’ for point-to-point MPLS connections or can encrypt at Layer 2 or Layer 3 or both, easy to configure without any down time for network access equipment.
Equipment Layer - 'Tunnel' Mode
Many times network to network security requires an encrypted ‘tunnel’ carrying Ethernet packets over a pre-defined network path. The BlackDoor GIG permits user creation of a destination table, encrypts the entire incoming packet, and adds the appropriate destination address for correct network transport.
Specifications
LAN Network Interface
- Two 10/100/1GB Full Ethernet
- Auto negotiation or Configured Speed and Duplex
LAN Network Protocols Supported
- IP, TCP, UDP, ICMP
- Telnet
Interfaces
- RJ45 electrical
System Architecture
- Point-to-Point
- Point-to-Multi-Point
Performance
- JUMBO Ethernet Packet capability (9KB MTU)
- Full Duplex
- Low latency
- In Process Key Updates
Regulatory
- CE
- Safety -IEC60950
- EMC - CFR 47 Part 15 Sub Part B:2002, EN55022: 1994 + A1 & A2, EN55024, ICES-003 1997, CISPR 22 Level A
Management
- Telnet support with Edit and Paste Template Files
- Console Port for Out of Band Management
- SNMP support (MIB I, MIB II) with configured traps
- Remote configuration, monitoring, & reset
- Telnet support with Edit and Paste Template Files
Power
- 12-30 VDC, 1.0A.
- Locking Connector
- Optional -48V 0.25 Amp
- Hot Standby
Dimensions
- Dimensions: 9" (L) x 7.3” (W) x 1.50” (H)
Environmental
- 0° to 132° F (-10° to 50°C) operating
- 90% operating humidity (non-condensing)
- Optional Extended Temperature Range available
TFTP Online Upgrade Capable (FLASH ROMs)
- Fully operational during upgrade
- Optional Extended Temperature Range available
Encryption Algorithm
- AES 256-bit
- Fully Automatic key management - 1 minute to 42 day re-key interval without interruption
- Hardware Random Number Generator
- Full Duplex real time encryption
Ordering Information
Chassis Slot Card: BlackDoor GIG
Rack Mount & Power Supply Options:


Part No.
Description
BlackDoor GIG Standalone
007-1010-GIG-xx*
BlackDoor Server, Gigabit Ethernet Encryptor AES Bridge or Tunnel, supports up to 20 remote BlackDoor (Server or Client) Connections. *Note: xx = number of remote BlackDoor Connections to be supported (01-20)
007-1010-GIG-CL
BlackDoor Client, Gigabit Ethernet Encryptor AES Bridge or Tunnel, must communicate with BlackDoor serverGigabit Ethernet Encryptor AES Bridge or Tunnel, must communicate with BlackDoor server
007-1010-GIG-01
BlackDoor Single-Client Server, Gigabit Ethernet Encryptor AES Bridge or Tunnel, supports 1 remote BlackDoor Client Connection
BlackDoor GIG Slot Card
CH-007-1010-GIG-20
BlackDoor Server, Gigabit Ethernet Encryptor AES Bridge or Tunnel, supports 20 remote BlackDoor (Server or Client) Connections - Slot Card Version
CH-007-1010-GIG-CL
BlackDoor Client, Gigabit Ethernet Encryptor AES Bridge or Tunnel, must communicate with BlackDoor server - Slot Card Version
CH-007-1010-GIG-01
BlackDoor Single-Client Server, Gigabit Ethernet Encryptor AES Bridge or Tunnel, supports 1 remote BlackDoor Client Connection - Slot Card Version
Power Supply Options
Power Supply Options
094-2418
90-220 VAC Universal International/Domestic Adapter
094-2418-R
DUAL REDUNDANT, 90-220 VAC Adapter
094-N48V
Internal Power Module, -48 VDC Screw Terminals
094-N48V-02
DUAL REDUNDANT, -48 VDC Screw Terminals
094-1500
WIREDC Option, +24 VDC Screw Terminals
094-WIREDC-R
DUAL REDUNDANT, +24VDC
Rack Mount Options
Rack Mount Option
095-1000
Rack Mount Kit - for single 7" products (Fits both 19" and 23" racks)
095-2000
2 unit 19" x 1RU Rack Mount Kit for 7" products
095-3000-RTANG
Right Angle Wall Mount Bracket Kit